Block Cyber Threats
 The 2014 Application Usage and Threat Report, prepared annually by Palo Alto Networks with client data, found that common sharing applications, such as email, social media, file sharing, etc., delivered 32% of all threats found (exploits and malware), and 19% of all code execution exploits found.
The 2014 Application Usage and Threat Report, prepared annually by Palo Alto Networks with client data, found that common sharing applications, such as email, social media, file sharing, etc., delivered 32% of all threats found (exploits and malware), and 19% of all code execution exploits found.
With this said, any Network Manager or Network Security Engineer wants to know, “How do I block or eliminate these threats?” A traditional port blocking firewall is nearly useless in this regard. I like Palo Alto Networks approach, which is essentially, “Control the application. Block the threat.”
According to Palo Alto Networks:
 “Applications are integral to virtually all cyber threats. In some cases, the application is the threat, such as a botnet communicating via a peer-to-peer network. In other cases the threat is enabled by an application that provides a vector for the threat or obscuring it from security solutions, such as an SSL encrypted browser session that obscures the delivery of malware.
“Applications are integral to virtually all cyber threats. In some cases, the application is the threat, such as a botnet communicating via a peer-to-peer network. In other cases the threat is enabled by an application that provides a vector for the threat or obscuring it from security solutions, such as an SSL encrypted browser session that obscures the delivery of malware.
By leveraging App-ID™, Palo Alto Networks provides visibility into all applications, where they can be controlled by policy and fully inspected for threats. Undesirable applications such as P2P file sharing, external proxies or circumventors, can be summarily blocked, or limited to the few users with a valid use case. Additionally, staff can easily restrict applications by their ability to tunnel other applications, transfer files, or history of being used by malware. These controls can instantly reduce the attack surface of the enterprise. Applications that are permitted can be controlled and inspected at a very granular level for viruses, spyware and vulnerability exploits. App-ID enhances the threat prevention logic through the use of more than 100 application and protocol decoders, which further reveal exactly where to look for different types of threats.” (The above quote was excerpted from the Palo Alto Networks Threat prevention Data Sheet.)
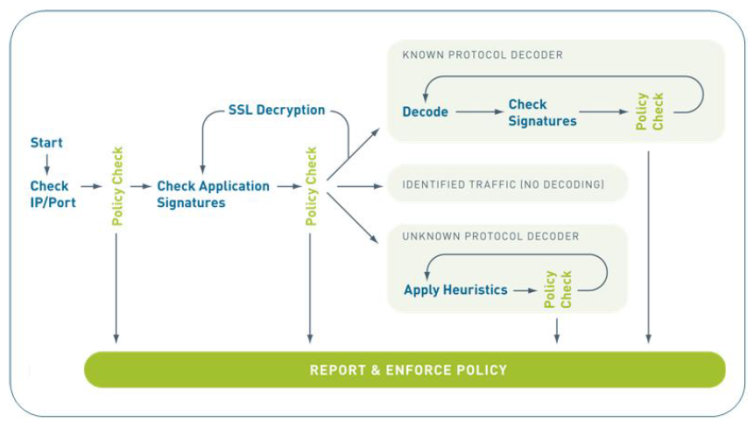
Palo Alto Networks Next Generation firewall has integrated the ability to search for application specific threats and Intrusion attempts into their core firewall, with Single-PassTM architecture. This enables their firewall to provide best of breed IPS and threat prevention at wire-speed scalable beyond 10 GB. Speed and capability are crucial components, but what really make revolutionary technology effective is that it is easy to implement and manage, even for companies with minimal network security experience.
